Certification Program in Offensive Cyber Techniques: Red Team Mobile Security & Dark Web
- International Cyber Hub Exposure
- Cyber War Room Experience
- Mentoring by Industry expert and Ex-Law Enforcement officials
- National Media Coverage
- Guaranteed Internship with Industry Exposure
- Pre-Placement Opportunities
- Placement Assistance
Apply Now
Download Brochure
Jun-Jul 2024 Cohort in Full Swing!

- Aug2024 Cohort Starting Soon
Limited Seats Remaining! Enroll Now!
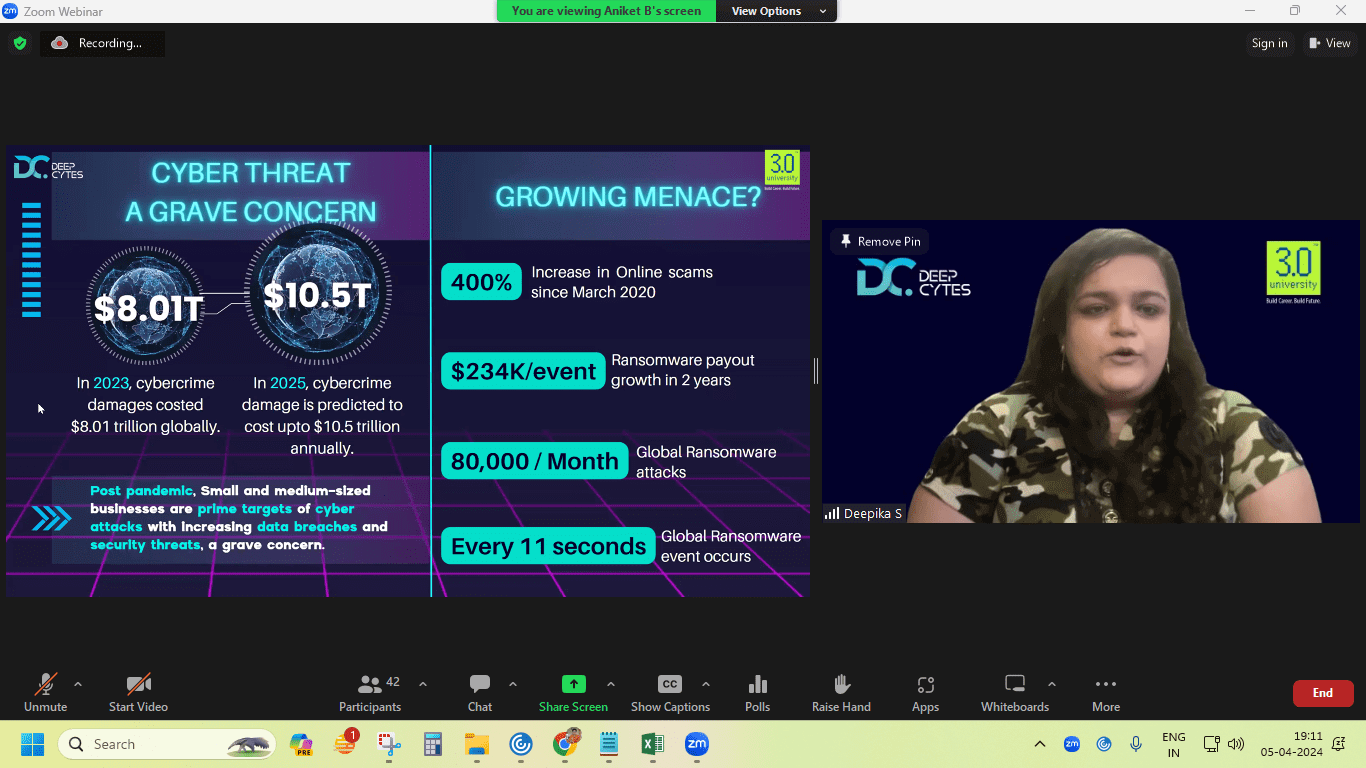
In 2023, cybercrime accounted for USD $8.01 trillion in damages globally – by 2025 this is estimated to increase to US $10.5 trillion.
As of 2024, India has a shortage of 8 lakh cybersecurity professionals
Employment in the cybersecurity field is projected to grow 31% in this decade – much faster than average across all occupations.
Demand for cybersecurity professionals has surged, leading to higher salaries and better career prospects – ranging from ₹6 to 18 LPA.
Hiring PARTNERS












And many more...
Program Key Highlights
- Blended Approach
- + 70 Hours of Training Content
- Live Mentoring Sessions/Week
- 6 Month Experiential Learning
- Guided Labs
- Capstone Project Development
- Guaranteed Internship
- Placement Assistance
- Professional Certification
About DeepCytes
DeepCytes is an award-winning UK-headquartered AI-enabled Cyber Intelligence company that deals with the evolving nature of Cybercrimes through Ransomware Protection, Forensics, and Training. With the team coming from a background of the Hon’ble Chief Minister of the State of Maharashtra’s Office and Law Enforcement, DeepCytes has carefully crafted an ecosystem build-up to help create cyber resilience in your environment. DeepCytes is a 95+ member firm with professionals from engineering and law enforcement backgrounds, enabling our goal for Cyber-Intelligence, and setting a new standard in tradecraft for cyber investigations, forensics, and being the cyber sentinel for the masses.
Apply Now
Program Overview
The Specialization comprises of 7 courses covering two verticals:
1. Red Team Mobile Security
Tailored to meet the evolving challenges of securing mobile applications and devices, this program offers a hands-on approach to mobile penetration testing, app security analysis, and vulnerability discovery. Delve into the intricacies of both iOS and Android platforms, equipping yourself with the skills needed to defend against cyber threats in the mobile environment.
Highlights
Focus specifically on mobile security, addressing the unique challenges and vulnerabilities associated with both iOS and Android platforms. Immerse yourself in a curriculum designed to hone your skills in securing mobile applications and devices.
Gain practical experience in mobile penetration testing, learning to identify and exploit vulnerabilities in mobile applications. Navigate through real-world scenarios to understand the complexities of securing mobile ecosystems.
Explore the nuances of security on both Android and iOS platforms. Understand the fundamental differences and similarities, enabling you to craft tailored security strategies for each operating system.
Master the art of conducting bug bounty penetration testing on the Google Play Store. Learn how to identify and responsibly disclose vulnerabilities in mobile applications, contributing to the security of widely used platforms.
Delve into the world of Mobile Remote Access Trojans (RATs) and attribution. Acquire expertise in attributing and analyzing mobile-based threats, a crucial skill for cybersecurity professionals defending against sophisticated attacks.
Program Outcomes:
➤ Proficiency in Mobile App Security: Develop a comprehensive understanding of mobile application security, enabling you to assess and secure applications on both Android and iOS platforms. Acquire the skills needed to identify and remediate vulnerabilities effectively.
➤ Dual Platform Expertise: Gain expertise in both Android and iOS security, allowing you to address the unique challenges posed by each operating system. Become a versatile professional capable of securing a wide range of mobile environments.
➤ Bug Bounty Recognition: Position yourself as a recognized expert in mobile application security with a focus on bug bounty programs. Acquire the knowledge and skills to contribute to the security of major app platforms.
➤ Mobile Threat Intelligence: Acquire advanced knowledge in Mobile Remote Access Trojans (RATs) and threat attribution. Understand the tactics used in mobile-based attacks, enhancing your ability to identify and respond to sophisticated threats.
➤ Practical Application of Skills: Develop practical skills through hands-on labs and real-world scenarios, ensuring that you are well-prepared to address the challenges of mobile security in a professional setting.
2. Dark Web
This section goes beyond exploration, delving into the intricacies of the Deep Web, Dark Web, and associated security practices. Gain expertise in navigating safely with tools like TOR and Tails, understand the nuances of cryptocurrency usage, and adopt messaging anonymity strategies. The Deep & Dark Web course bundle equips participants not only with the knowledge to explore these clandestine environments responsibly but also with the skills to safeguard their identity and data.
Highlights
Learn the ins and outs of TOR (The Onion Router) and Tails (The Amnesic Incognito Live System), essential tools for anonymous and secure internet browsing. Understand how to configure and use these tools effectively for Deep & Dark Web exploration.
Explore the role of cryptocurrency in the Deep & Dark Web. Gain an in-depth understanding of how cryptocurrencies are used, traded, and the associated security considerations. Learn about blockchain technology and its impact on anonymity.
Delve into messaging anonymity, exploring techniques for secure communication in the Deep & Dark Web. Understand the use of encrypted messaging platforms and the importance of maintaining anonymity in online communications.
Develop privacy-centric browsing practices specific to the Deep & Dark Web. Learn how to avoid common pitfalls, protect your identity, and mitigate the risk of exposure while engaging in online activities.
Gain insights into the legal and ethical aspects of Deep & Dark Web exploration. Understand the boundaries of responsible usage, distinguishing between legal and illegal activities, and adhering to ethical standards while navigating these hidden environments.
Program Outcomes:
➤ TOR and Tails Proficiency: Acquire the skills to navigate the Deep & Dark Web securely using TOR and Tails. Learn to configure and use these tools effectively, ensuring your online activities remain anonymous and protected.
➤ Crypto Literacy: Develop a comprehensive understanding of cryptocurrency usage in the Deep & Dark Web. Learn how to use, trade, and navigate the associated security landscape, including the impact of blockchain technology on anonymity.
➤ Messaging Anonymity Mastery: Become adept at secure communication strategies. Understand the importance of messaging anonymity, learn to use encrypted platforms effectively, and ensure your online conversations remain private and protected.
➤ Advanced Privacy Practices: Implement advanced privacy practices specific to Deep & Dark Web browsing. Develop the skills to protect your identity, avoid potential risks, and navigate online spaces with a heightened awareness of privacy considerations.
➤ Ethical Deep & Dark Web Exploration: Graduate with a strong understanding of the legal and ethical aspects of Deep & Dark Web exploration. Navigate these environments responsibly, distinguishing between lawful and unlawful activities, and contributing to a safer online community.
Learning Path
Download Brochure
1.1 Introduction to Android Security
1.2 Navigating the Android Environment
1.3 Attacks on Android Platforms
1.4 Reverse Engineering and Malware Creation for Android
1.5 Conclusion and Recap
2.1 Getting Started
2.2 Analyzing Vulnerabilities
2.3 Drozer in Action
2.4 Bug Bounty Hunting Strategies
3.1 Setting Up Your Lab Environment
3.2 Exploring Mobile Backdoors
3.3 Essential Android Studio Skills
3.4 Java Programming Essentials
3.5 Foundations of iOS Development
3.6 Understanding Rooting and Jailbreaking
3.7 Android Reverse Engineering Techniques
3.8 iOS Reverse Engineering Strategies
3.9 Securing Firebase in Cloud Hacking
3.10 Capture The Flag (CTF): Hacking Banking Apps
3.11 Mobile Device In-Network Attack Strategies
4.1 Introduction
4.2 Application Security
4.3 Connection Obfuscation Techniques
4.4 Secure your Device
4.5 Messaging & Encryptions
4.6 Post-Event Recovery
5.1 Setting Up Your Lab
5.2 Gathering Information for Exploits
5.3 Exploiting APK Modifications
5.4 Exploiting Insecure Authentication
5.5 Exploiting Insecure Storage
5.6 Exploiting Broadcast and Content Providers
5.7 General Tips for Bug Bounty Hunting
6.1 Introduction to Online Privacy
6.2 Concepts of the Dark Web
6.3 Exploring the Tor Browser
6.4 Ethical Considerations & Use
7.1 Using Tails - The Amnesic Incognito Live System
7.2 Accessing the Dark Net - Entry Points
7.3 Private and Anonymous Communication - Email
7.4 Private and Anonymous Communication - Instant Messaging
7.5 Managing Files and Sharing Securely
7.6 Exploring Encryption
7.7 Understanding Cryptocurrencies
7.8 Bitcoin - The Cryptocurrency Giant
7.9 Monero - Privacy-Centric Cryptocurrency
7.10 Exploring Qubes OS
Pedagogy
Self-Paced Training Content (Video Lectures + Study Material + Guided Labs + Instructional Manuals + Self-Assessment) along with Live Mentoring Sessions and Capstone Projects ensure the students have an all-encompassing grasp on the subject.
Nature of Internship
● The nature of the internship will be a hybrid model for 3-months or more depending on performance.
● Internship would be in the domain of Red Teaming and Dark Web Labs. During this internship, Students would employ the skillsets during live projects that they have learnt throughout the course.
● Top performers may get the opportunity to work on research and live cases with industry experts and law enforcement bodies and obtain Letters of Appreciation (LOA) upon successful completion of project(s).
Free Program Counselling
We are happy to help you
By providing your contact details, you agree to our Terms and Conditions & Privacy Policy
Program Fees
Jun-Jul 2024 Cohort in Full Swing, Limited Seats Remaining!
Corporate Discount for Working Professionals
Scholarship for Students
Program Fees
₹65,000/-
(Inclusive of all Applicable Taxes)
Apply Now