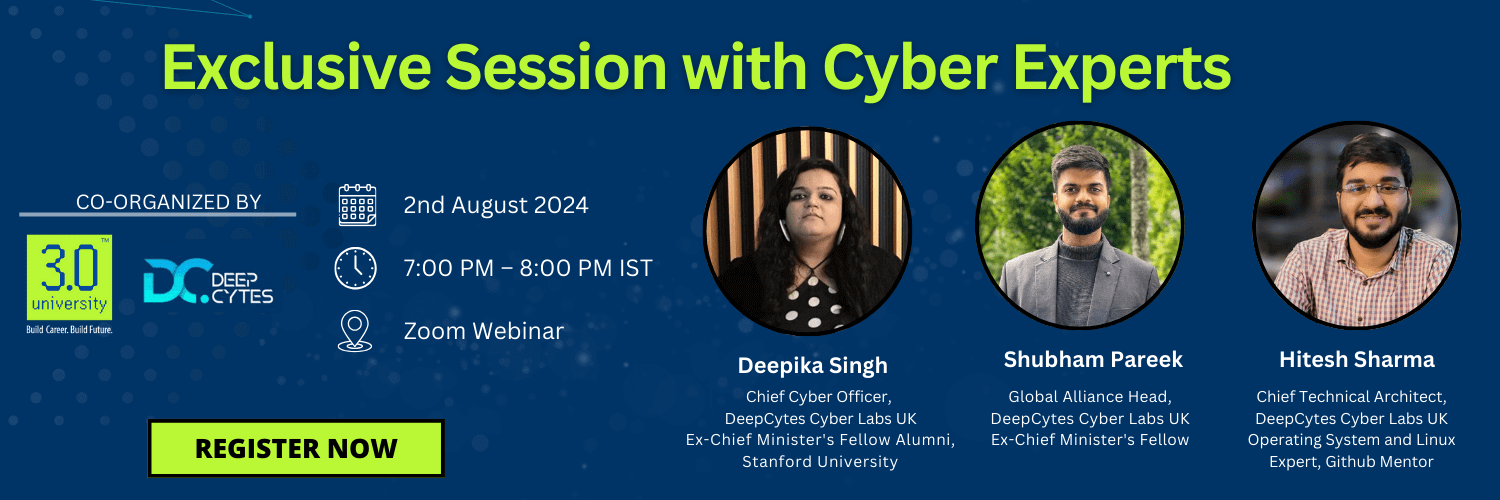
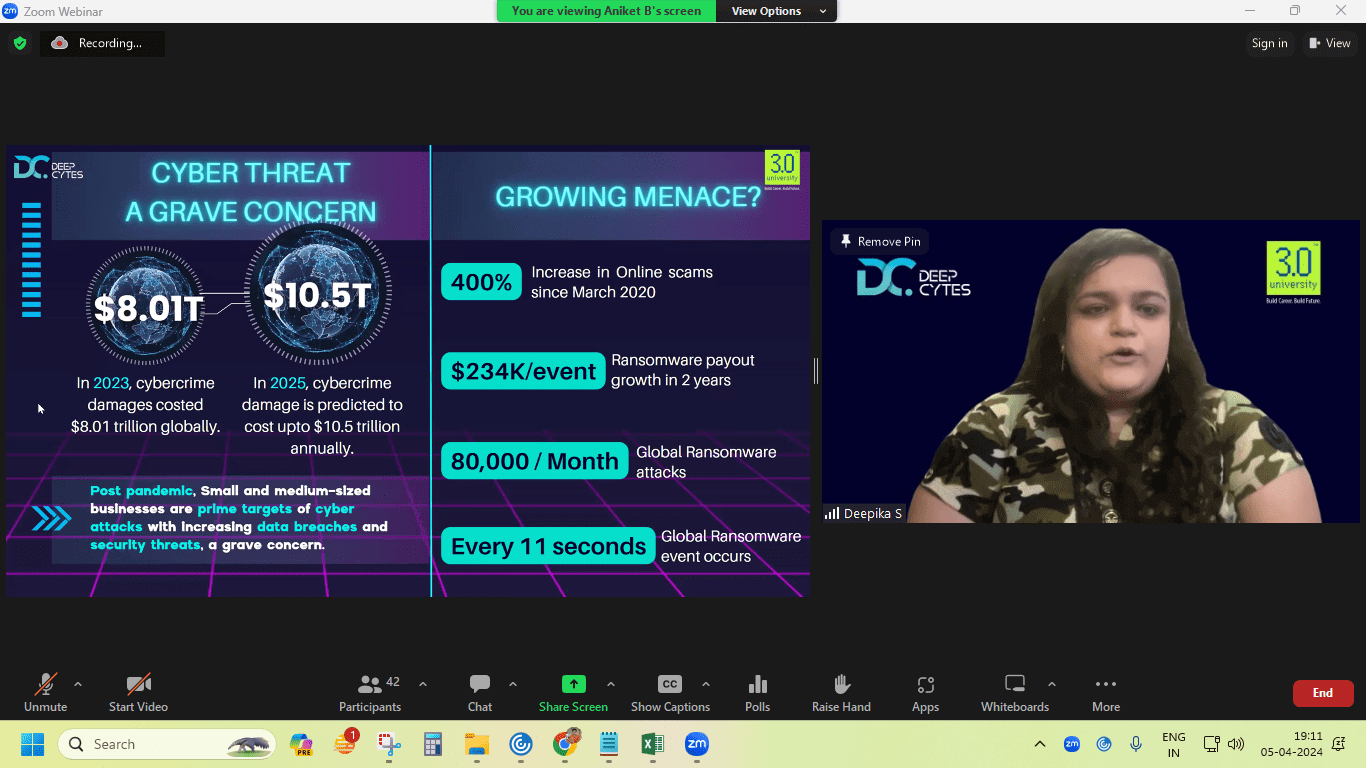
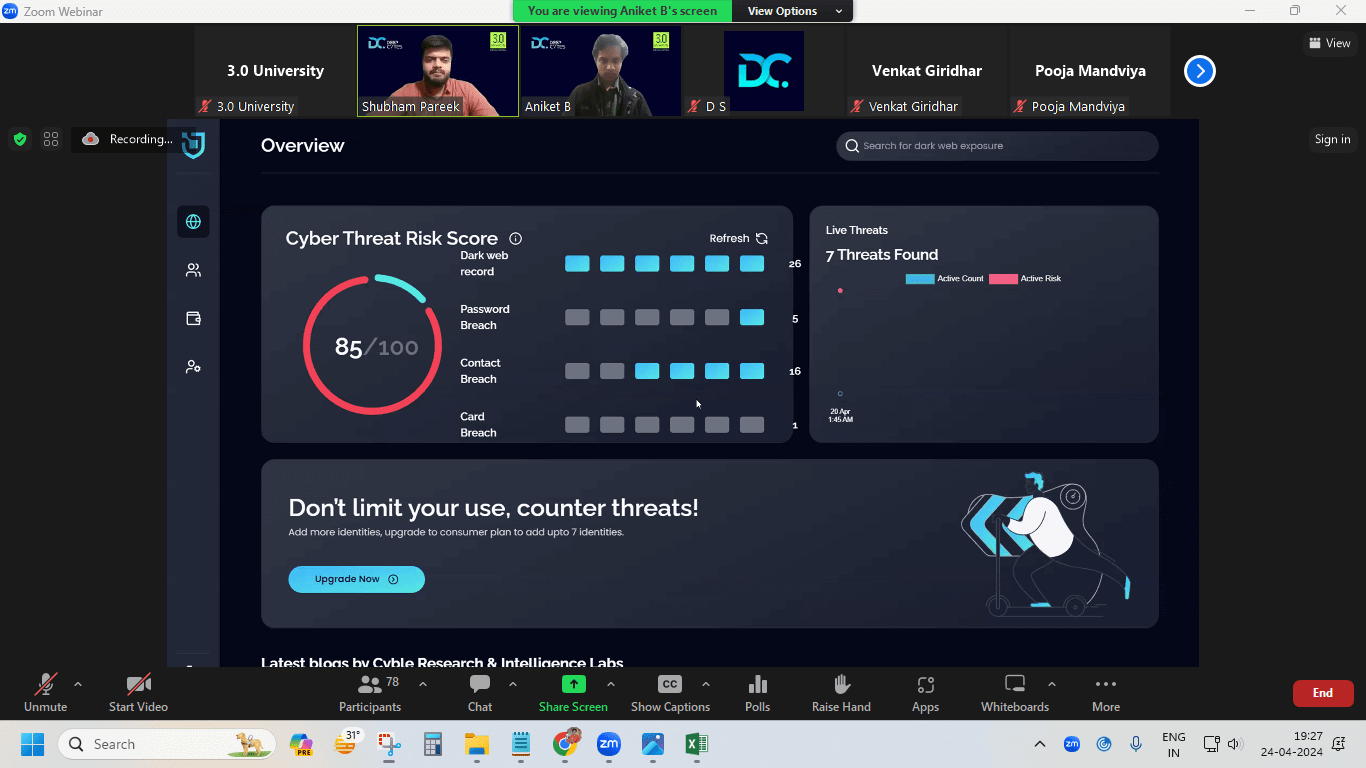
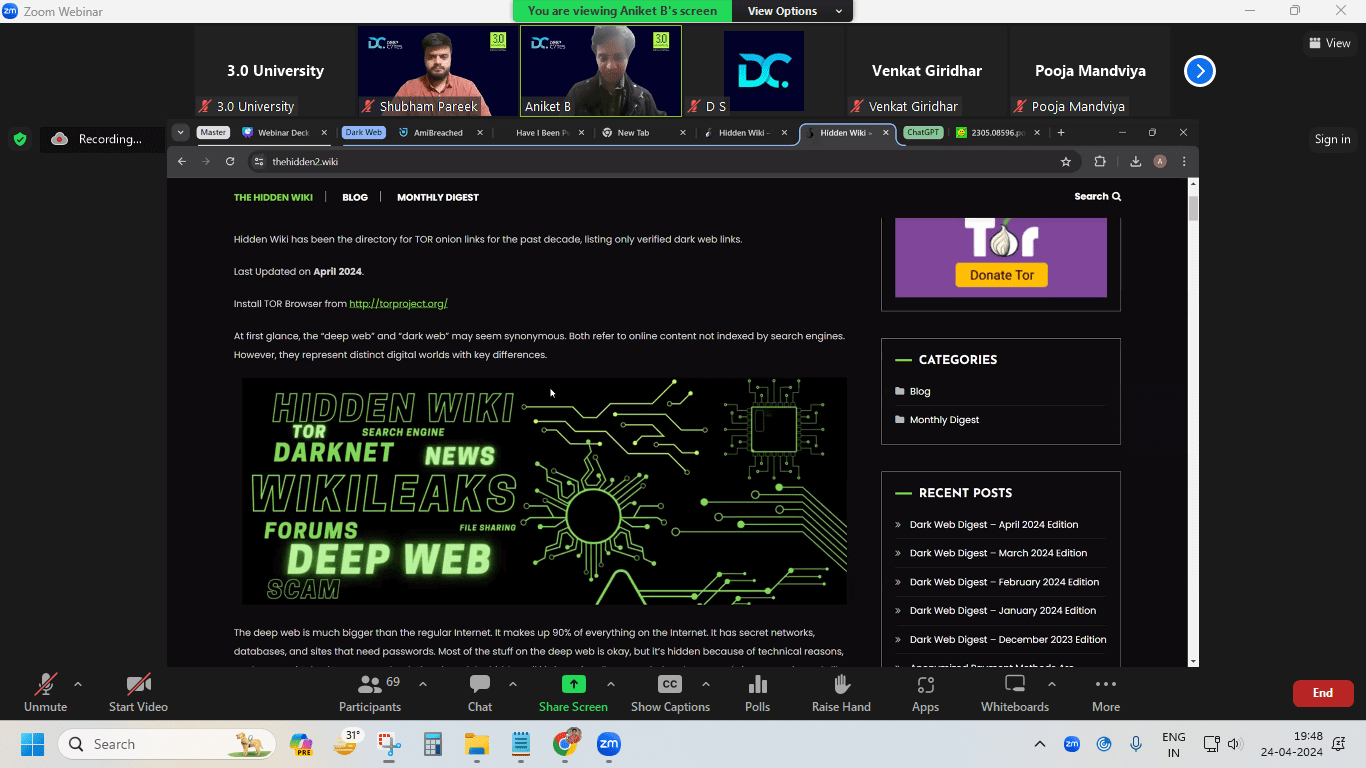
HomeCertification Program in Offensive Cyber Techniques


Certification Program in Offensive Cyber Techniques: Red Team Mobile Security & Dark Web
- International Cyber Hub Exposure
- Cyber War Room Experience
- Mentoring by Industry expert and Ex-Law Enforcement officials
- National Media Coverage
- Guaranteed Internship with Industry Exposure
- Pre-Placement Opportunities
- Placement Assistance
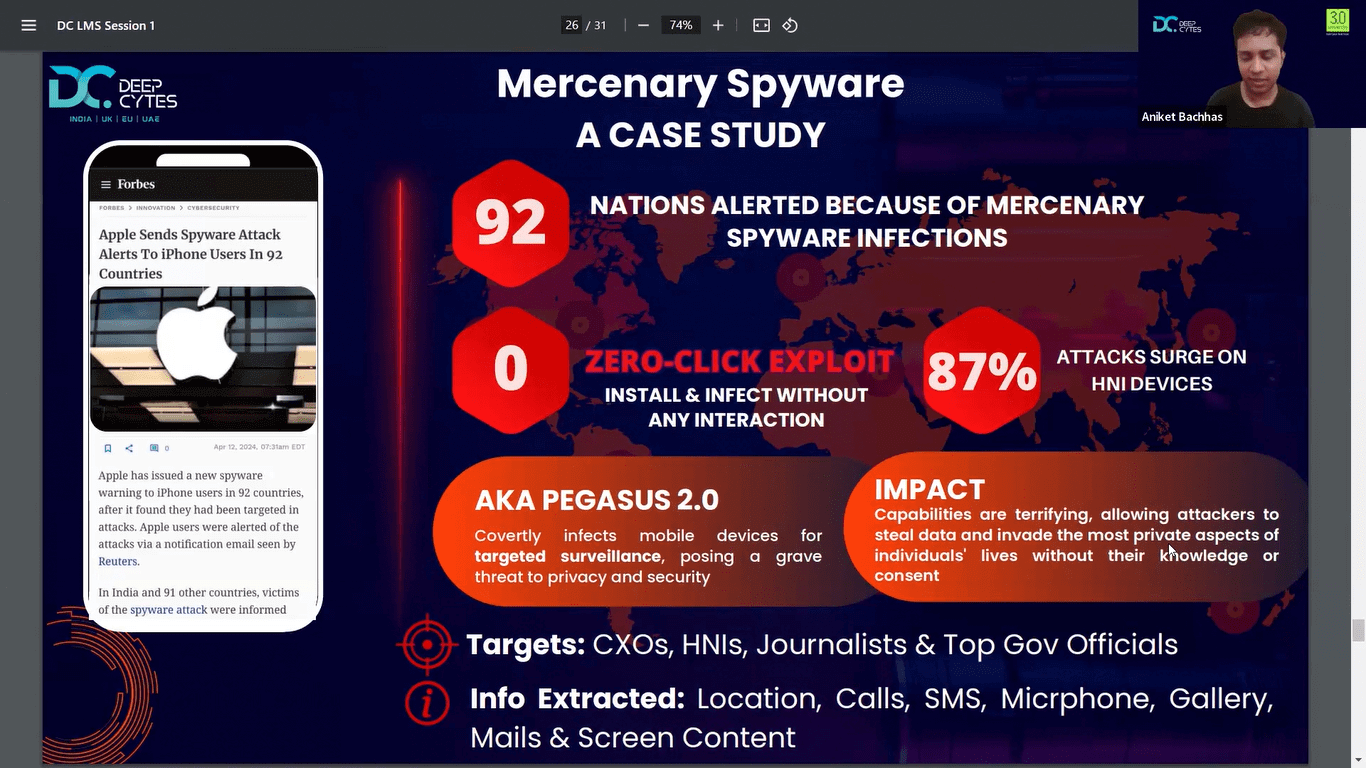

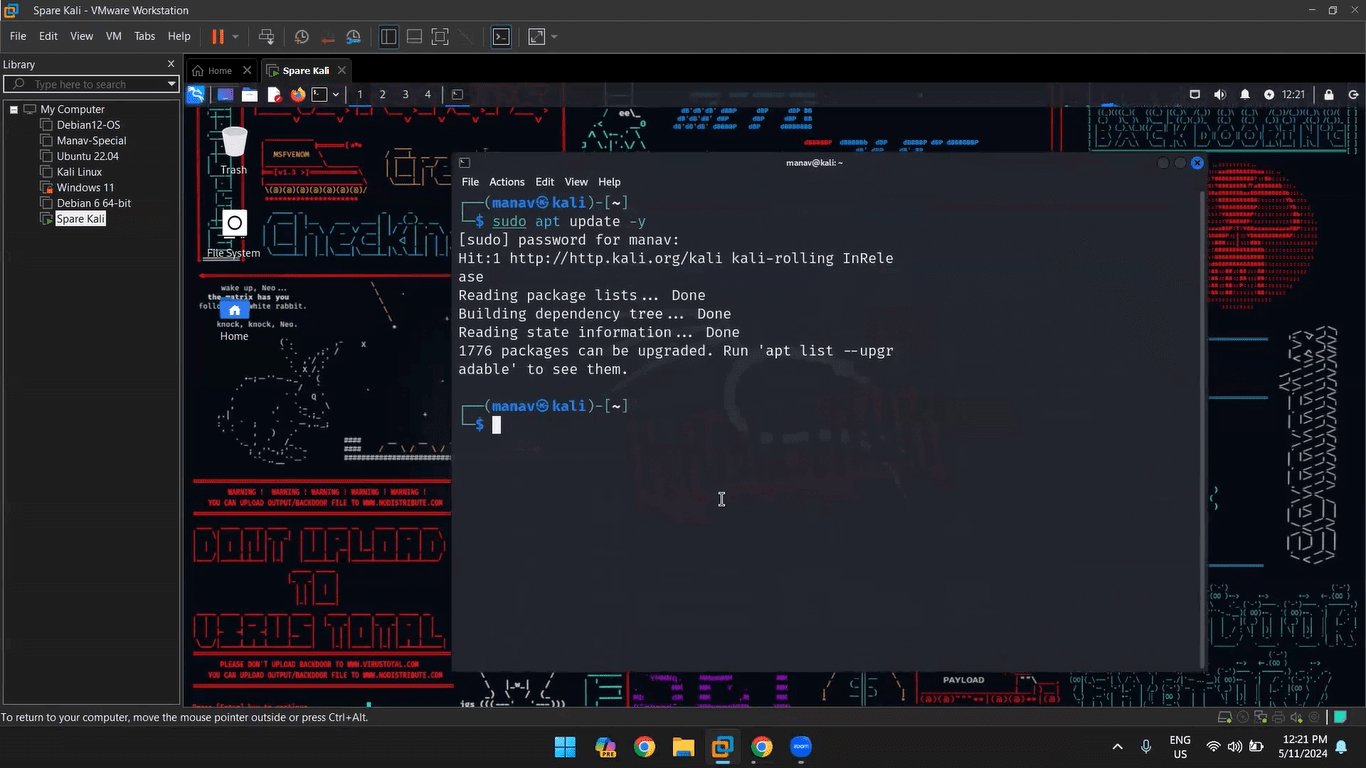
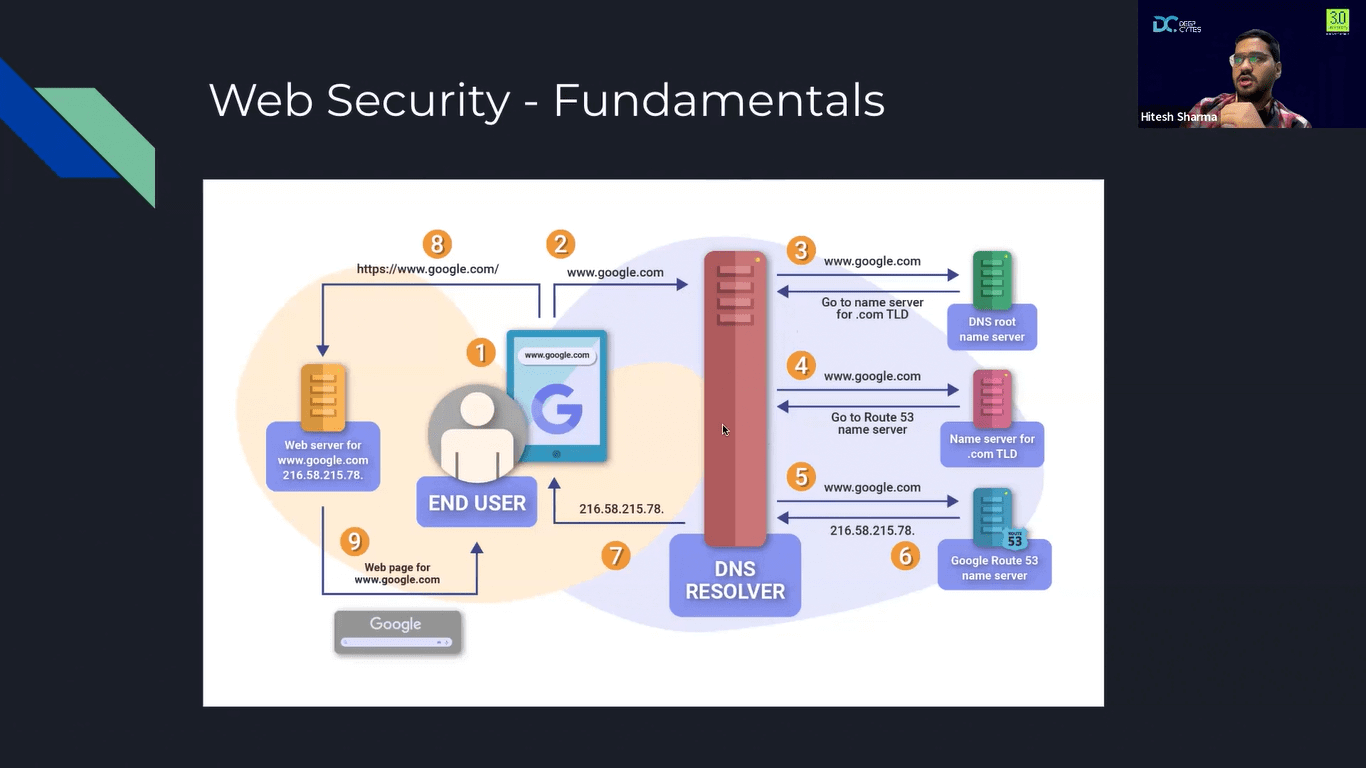
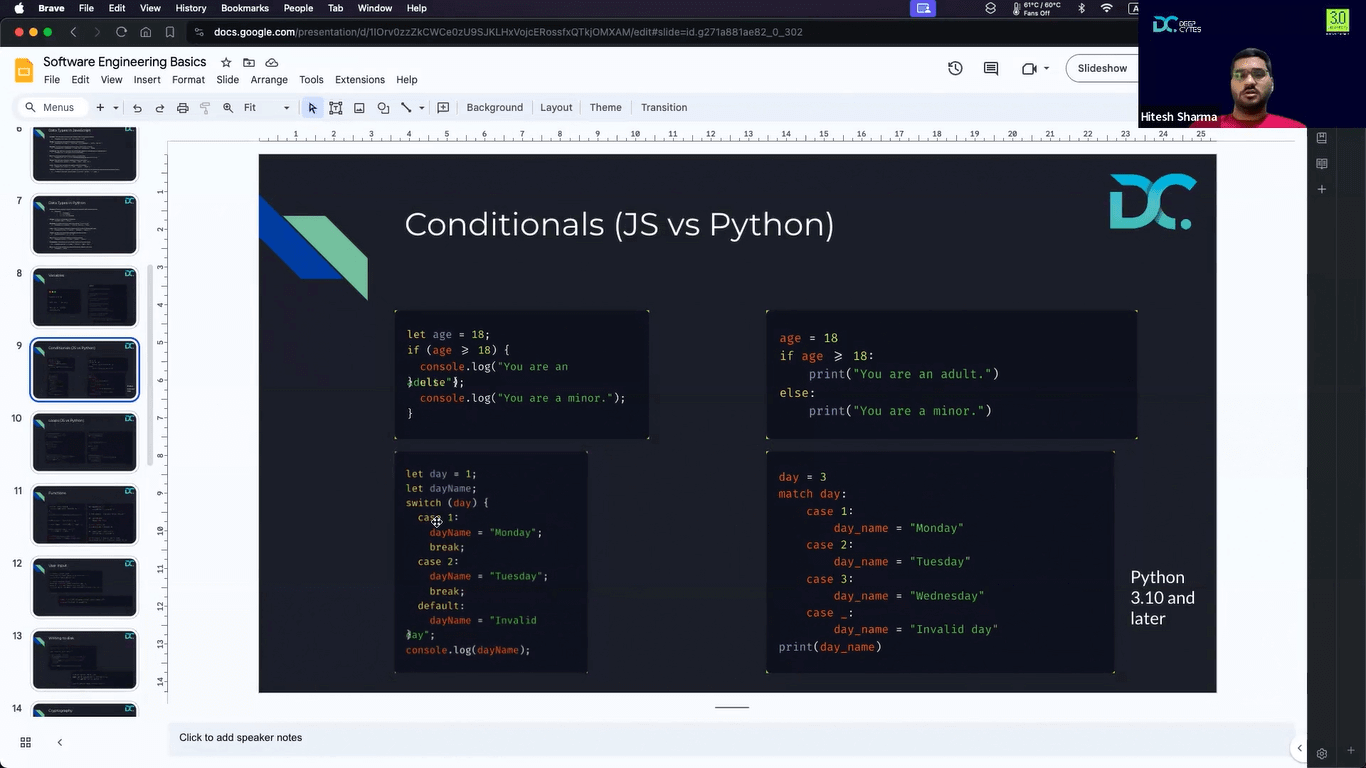
- Cohort Starting Soon