
How to Build Enterprise Cyber Security Framework?
- Posted by 3.0 University
- Categories Cyber Security
- Date December 6, 2024
- Comments 0 comment
In today’s rapidly transmuting digital world, robust cybersecurity practices are more important than ever. As organizations depend more on digital systems, it is crucial to create a clear method for handling cybersecurity. A strong, well-fortified cybersecurity framework acts like a guide for dealing with information security risks and making sure that the organization’s goals match its technical structure.
Creating this framework requires a deep understanding of risk types, including identifying and classifying different IT risks, as discussed in [citeX]. This basic knowledge helps organizations use strategic responses to risks—accepting, reducing, or transferring them—while building a culture that values security.
Therefore, the connection between risk assessment, security strategy development, and compliance can greatly improve an organization’s ability to withstand possible cyber threats, creating a proactive cybersecurity stance that is necessary for long-term success.
Importance of a Cybersecurity Framework in Modern Enterprises
Creating a strong cybersecurity framework is now a key part of business strategy in the current digital world, rather than just an afterthought. By using set methods to find and lessen cyber risks, companies can more effectively handle complicated regulatory issues and act ahead of new threats.
A recent study shows that cybersecurity frameworks help manage digital assets systematically, assisting security managers in reducing risks in various settings. Specifically, frameworks like the NIST Cybersecurity Framework (CSF) enable businesses to comprehend, handle, and decrease their cybersecurity risks while safeguarding their networks and data.
This organized method is crucial for matching cybersecurity efforts with larger business goals, which ultimately promotes a mindset of strength and flexibility. Moreover, these frameworks improve communication between IT teams and top management, ensuring that cybersecurity is part of the overall business plan.
This integration holds significant importance as modern businesses face increasingly sophisticated cyber threats that challenge their operational stability. Therefore, creating and applying an effective cybersecurity framework is crucial for keeping a competitive edge in the digital age, as shown in the detailed risk taxonomy outlined in [extractedKnowledge1].
Assessing Organizational Needs
Knowing what an organization needs is important for making a successful cybersecurity plan. A detailed check helps find weak points, which lets companies adjust their security efforts. This step should look at the tools they have now, spot missing technology or skills, and get a grasp on how the organization operates.
By looking at these details, organizations can make their cybersecurity plans match their business goals and better manage risks. The IT Risk Taxonomy, as demonstrated in [citeX], serves as a valuable tool in this process, categorizing various IT risks and emphasizing the significance of aligning IT controls with business functions.
This way, organizations can better spot and meet their needs, improving their security and ability to bounce back from threats. This smart method not only boosts defences against cyber risks but also helps create a mindset of security awareness and active risk management in the organization.
Organization Size | Budget Allocation (%) | Vulnerabilities Identified | Employee Training (%) |
Small (1-50 employees) | 15 | 10 | 30 |
Medium (51-200 employees) | 25 | 20 | 50 |
Large (201-1000 employees) | 35 | 35 | 70 |
Enterprise (1001+ employees) | 50 | 50 | 80 |
Organizational Cyber Security Needs Assessment Data
Key Assets and Threats
In the field of enterprise cybersecurity, it is very important to understand key assets and related threats for good risk management. Companies need to perform deep assessments to find key assets, which include data, network systems, and intellectual property.
Cyber attackers often target these valuable assets as their primary targets. Using insights from frameworks like those shown here, where IT risks are sorted, can improve the identification process by giving clear methods to analyze different risk categories.
Also, looking at potential threats means checking both outside and inside factors. For instance, the constant shifts between new vulnerabilities and organizational capabilities necessitate a comprehensive security approach, as previously mentioned. Understanding this relationship allows companies to better focus their defences, ensuring the wise use of resources to mitigate the biggest threats and safeguard essential assets.
Asset Threat | Description | Impact | Likelihood |
Sensitive Customer Data | Personal information that must be protected from unauthorized access. | High | Medium |
Financial Data | Data related to company finances that could lead to financial loss if compromised. | High | High |
Intellectual Property | Trade secrets and proprietary information critical for competitive advantage. | High | Medium |
Critical Infrastructure | Systems essential for operations, such as power, water, and communication. | High | Medium |
Employee Credentials | Login information that can lead to unauthorized access to systems. | Medium | High |
Physical Assets | Devices and equipment that store or process data, like servers and laptops. | Medium | Medium |
Third-Party Services | Outsourced services that may expose the organization to external vulnerabilities. | Medium | High |
Identifying Key Cyber Security Assets and Threats
Designing the Cybersecurity Framework
A strong way to make a cybersecurity plan needs a deep understanding of risks in the organization and a fit with how the business is structured. This involves looking at current business needs and doing a detailed gap analysis to find weaknesses and areas that need fixing. Including a clear risk management plan, as shown in frameworks listed in the IT Risk Taxonomy, helps ensure that businesses can handle new threats well.
Companies also need to use flexible security ideas, as talked about in the Dynamic Security Approach, which focus on being adaptable and working together across different parts of the business.
As cybersecurity keeps changing, using these frameworks helps not only strengthen defences but also ensure that the organization meets regulatory requirements. For example, “Aligning your organization’s Zero Risk strategies with established cybersecurity and regulatory compliance frameworks is a necessity,” sums up the importance of combining these standards into one strong plan (“Aligning your organization’s Zero Risk strategies with established cybersecurity and regulatory compliance frameworks is a necessity.) The goal is to create a robust security posture that not only protects your assets but also ensures you meet the critical standards set by regulatory bodies.” (Dummies.com).
By doing this, organizations can create strong security measures that match their specific operational needs.
Component | Description | Importance | Example |
Identify | Asset management, risk assessment, governance, and business environment. | Establishing a foundational understanding of security needs and resources. | Conducting regular risk assessments to identify potential vulnerabilities. |
Protect | Access control, data security, and awareness training. | Implementing safeguards to protect sensitive information. | Training employees on phishing awareness and secure password practices. |
Detect | Anomalies and events, continuous monitoring. | Recognizing potential security incidents as they occur. | Utilizing intrusion detection systems to monitor network traffic. |
Respond | Response planning, communications, analysis, mitigation. | Managing the response to detected security incidents effectively. | Establishing a communications plan for informing stakeholders during a breach. |
Recover | Recovery planning, improvements, communication. | Restoring capabilities and services after an incident. | Conducting post-incident reviews to improve response procedures. |
Cybersecurity Framework Components
Integrating Enterprise Architecture with Cybersecurity Principles
Bringing together cybersecurity principles with enterprise architecture helps organizations stay strong against new threats. When these two domains collaborate, they foster a comprehensive approach to risk management, ensuring that cybersecurity is an integral aspect of the organization’s design rather than an add-on.
By looking closely at how different technologies, processes, and people connect, organizations can build a space where security is a fundamental part of enterprise architecture. The IT Risk Taxonomy framework illustrates this link by categorizing risks at various levels, facilitating thorough assessment and response.
A solid cybersecurity framework is not just about traditional defence; it also includes flexible parts that change with new threats, as shown in the Dynamic Security Approach. This cooperation allows organizations not just to meet rules but also to protect sensitive information ahead of time, showing a strong risk management method that values planning and new ideas.
Conclusion
Building a strong cybersecurity framework for a business is not just about technology; it is a broad commitment to protecting the organization’s assets from changing threats. An effective framework combines thorough risk assessments with flexible response plans, as shown in the taxonomy detailed in [citeX].
This systematic approach ensures the identification and classification of risks, enabling organizations to devise tailored strategies for their mitigation. Additionally, using a flexible security approach, as noted in [extractedKnowledgeX], highlights the importance of ongoing adjustment and teamwork throughout the organization.
By encouraging a culture that values security and resilience, businesses can improve their ability to tackle challenges. In the end, aligning cybersecurity goals with business objectives, as mentioned in [citeX], is vital for lasting success. This alignment makes sure that security efforts not only provide protection but also support the organization’s mission in a digital world, thus strengthening its overall structure.
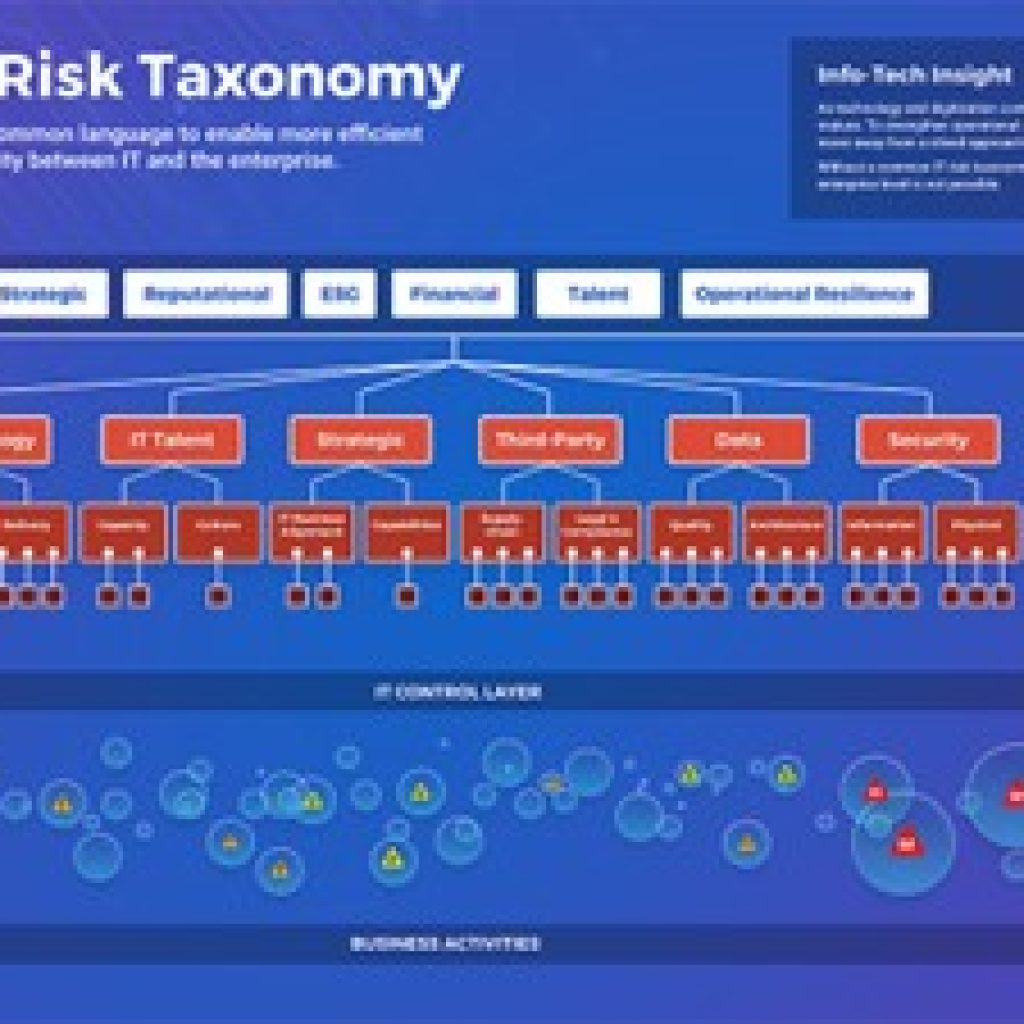
Image1. IT Risk Taxonomy Framework for Enterprise Risk Management
Future Trends and Continuous Improvement in Cybersecurity Frameworks
As businesses move through a more complicated digital world, the development of cybersecurity plans is very important. Future directions indicate a shift toward flexible and changing security methods that focus on resilience and constant improvement.
This flexibility will allow companies to react well to new dangers, like advanced persistent threats (APTs) and ransomware. A solid cybersecurity plan needs to include ongoing checks of risks and threat situations and fit with business structures.
Importantly, using artificial intelligence and machine learning in these plans will improve threat detection and response times. Additionally, encouraging involvement and teamwork at all levels of the company is crucial for building security awareness and shared duty.
The framework demonstrates a forward-thinking attitude by emphasizing the need to study threats and risks and enhance readiness. Such plans will make sure that companies not only protect themselves from existing dangers but also adjust and succeed in upcoming challenges.
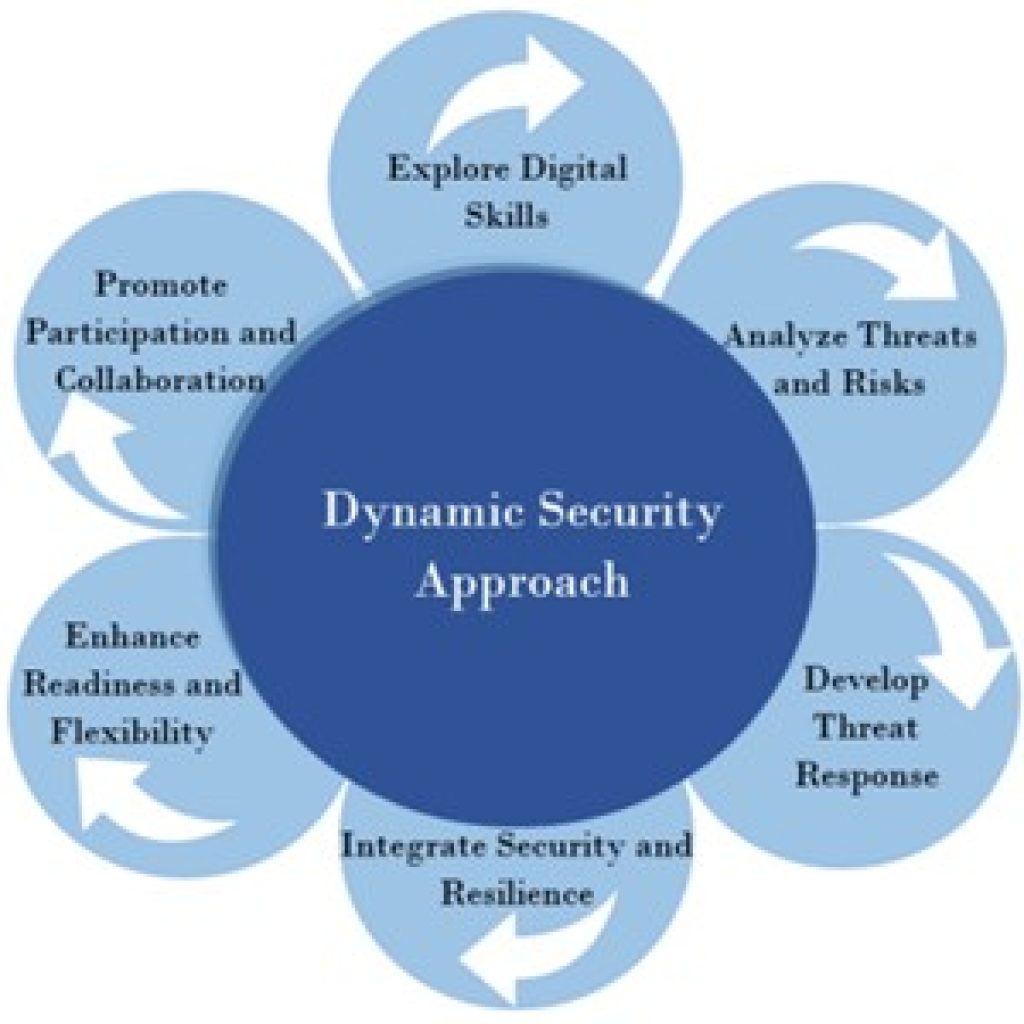
Image3. Framework for the Dynamic Security Approach
Year | Trend | Impact | Percentage Adoption | Source |
2023 | Increased AI Integration | Enhanced threat detection and response | 78 | Gartner |
2023 | Zero Trust Security Models | Reduced attack surface | 66 | Forrester Research |
2023 | Cloud Security Enhancements | Greater protection for cloud-based assets | 72 | CSA (Cloud Security Alliance) |
2023 | Regulatory Compliance Automation | Streamlined compliance and reporting | 62 | Ponemon Institute |
2023 | Employee Training and Awareness | Reduction in human error incidents | 69 | Cybersecurity & Infrastructure Security Agency (CISA) |
Cybersecurity Trends and Improvements (2023)
You may also like

Firewalls & Future of Cybersecurity Careers in 2025


