

Certified Ethical Hacker CEHv13
World's No.1 Ethical Hacking Certification, now with the power of Al
- Exclusive Preview: Experience the latest C|EH course content.
- Expert Guidance: Learn from industry leaders and experts.
- Networking Opportunities: Connect with like-minded professionals.
- Boost your task efficiency by 40% in your job role.
- C|EH v13 includes 4,000 tools and 550 attack techniques.
Exclusive Offer Ending Soon! Enroll Now to avail Scholarships upto ₹10,000. Seats are filling up fast—Reserve Yours Today!
Get Free Counselling Today
Gain More with CEHv13
Advance your career with CEH, now with added Al capabilities
Gain industry-ready skills by learning the multi-platform strategies and tactics used by today's most sophisticated cybercriminals (including Al) so you can identify system vulnerabilities before they do.
- 92% of employers prefer CEH graduates for ethical hacking jobs
- 95% chose CEH for career growth
- Modules are mapped to 49 cybersecurity job roles
- 4 in 5 companies say Al is a strategic priority
- 1 in every 2 professionals received promotions after CEH
What's New in CEHv13
Al-powered
The world's first ethical hacking certification to harness the power of Al.
Hands-on experience
Hone your skills in real-world scenarios through hands-on labs, where you practice attack vectors and master advanced hacking tools.
40% more efficiency
Learn Al-driven techniques to boost efficiency in cyber defense by 40% while streamlining your workflow
Power-packed, updated curriculum
Master the latest advanced attack techniques, trends, and countermeasures.
2x productivity gains
Advanced threat detection, enhanced decision-making, adaptive learning, enhanced reporting, and automation of repetitive tasks.
Real-world skills, proven mastery
Participate in monthly global hacking competitions, compete with your peers, and make it to the leaderboard.
CEHv13 Course Overview
The C|EH v13 is a specialized, one-of-a- kind training program that helps you gain expertise in ethical hacking, AI, and machine learning. With hands-on training labs, knowledge-based and practical exams, a mock ethical hacking engagement on live networks, and a global hacking competition, this program ensures you master the most in-demand skills needed to excel and stand out in the cybersecurity industry.
CEH Training Key Features
- Learn to Hack AI Systems Based on OWASP’s
- Master AI to Automate Ethical Hacking Tasks
- Boost your task efficiency by 40% in your job role.
- C|EH v13 includes 4,000 tools and 550 attack techniques.
-
Attain the World’s No.1 Credential in Ethical
Hacking, Now Powered by AI
Take the Scholarship Test
Participate in our Cybersecurity Scholarship Assessment to demonstrate your knowledge and readiness in the field. Based on your performance, we will offer a discount on CEH program to eligible participants.
Steps for Successful Scholarship Test Participation
- Step 1 : Download & Study the Cybersecurity Insights Handbook
- Step 2 : Prepare for the Scholarship Test through Handbook
- Step 3 : Appear for the Scholarship Test
- Step 4 : Complete the test in 15 minutes.
- Step 5 : Results Evaluation and Communication
Ethical Hacking Course Curriculum
Ethical Hacking Training in Mumbai
The CEH v13 course features 20 modules, blending essential cybersecurity skills with the latest tools and techniques. It integrates AI across all phases of ethical hacking, boosting efficiency in reconnaissance, gaining access, and more. With a mix of knowledge-based training and hands-on labs, you’ll gain real-world experience by working with live targets and systems, preparing you to apply your skills confidently in real scenarios.
Course Content
Learn the fundamentals and key issues in information security, including the basics of ethical hacking, information security controls, relevant laws, and standard procedures.
Learn how to use the latest techniques and tools
for foot printing and reconnaissance, a critical
pre-attack phase of ethical hacking
Learn different network scanning techniques
and countermeasures.
Learn various enumeration techniques, including Border
Gateway Protocol (BGP) and Network File Sharing
(NFS) exploits and associated countermeasures.
Learn how to identify security loopholes in a target organization’s network, communication infrastructure, and end systems. Different types of vulnerability assessment
and vulnerability assessment tools are also included.
Learn about the various system hacking methodologies used to discover system and network vulnerabilities, including steganography, steganalysis attacks, and how to cover tracks.
Learn about different types of malware (Trojan, viruses, worms, etc.), APT and fileless malware, malware analysis
procedures, and malware countermeasures.
Learn about packet sniffing techniques and their uses for discovering network vulnerabilities, plus countermeasures to defend against sniffing attacks.
Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
Learn about different Denial of Service (DoS) and Distributed DoS (DDoS) attack techniques, plus the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Learn the various session-hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Learn about firewalls, intrusion detection systems (IDS), and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures.
Learn about web server attacks, including a comprehensive attack methodology used to audit vulnerabilities in web server infrastructures and countermeasures.
Learn about web application attacks, including a comprehensive hacking methodology for auditing vulnerabilities in web applications and countermeasures.
Learn about SQL injection attack techniques, evasion
techniques, and SQL injection countermeasures.
Learn about different types of encryption, threats,
hacking methodologies, hacking tools, security tools, and countermeasures for wireless networks.
Learn mobile platform attack vectors, Android and
iOS hacking, mobile device management, mobile
security guidelines, and security tools.
Learn different types of Internet of Things (IoT) and operational technology (OT) attacks, hacking methodologies, hacking tools, and countermeasures.
Learn different cloud computing concepts, such as container technologies and serverless computing,
various cloud computing threats, attacks, hacking
methodologies, and cloud security techniques and tools.
Learn about encryption algorithms, cryptography tools, Public Key Infrastructure (PKI), email encryption, disk encryption, cryptography attacks, and cryptanalysis tools.
Beat Hackers in their Own Game with CEH v13
Master AI and Tools to Automate Ethical Hacking Tasks, to hack and defend against AI systems and boost your task efficiency by 40% in your job role.
















- Mid-Level Information Security Auditor
- Cybersecurity Auditor
- Security Administrator
- IT Security Administrator
- Information Security Analyst 1
- Infosec Security Administrator
- Cybersecurity Analyst level 1, level 2, & level 3
- Network Security Engineer
- SOC Security Analyst
- Network Engineer
- Senior Security Consultant
- Information Security Manager
- Senior SOC Analyst
- Solution Architect
- Cybersecurity Consultant
- Cyber Defense Analyst
- Vulnerability Assessment Analyst
- Warning Analyst
- All-Source Analyst
- Cyber Defense Incident Responder
- Research & Development Specialist
- Senior Cloud Security Analyst
- Third Party Risk Management
- Threat Hunting Analyst
- Penetration Tester
- Cyber Delivery Manager
- Application Security Risk
- Threat Modelling Specialist
- Web Application Penetration Testing
- SAP Vulnerability Management – Solution Delivery Advisor
- Ethical Hacker
- SIEM Threat Responder
- Product Security Engineer / Manager
- Endpoint Security Engineer
- Cybersecurity Instructor
- Red Team Specialist
- Data Protection & Privacy Officer
- SOAR Engineer
- AI Security Engineer
- Sr. IAM Engineer
- PCI Security Advisor
- Exploitation Analyst (EA)
- Zero Trust Solutions Engineer / Analyst
- Cryptographic Engineer
- AI/ML Security Engineer
- Machine Learning Security Specialist
- AI Penetration Tester
- AI/ML Security Consultant
- Mid-Level Information Security Auditor
- Cybersecurity Auditor
- Security Administrator
- IT Security Administrator
- Information Security Analyst 1
- Infosec Security Administrator
- Cybersecurity Analyst level 1, level 2, & level 3
- Network Security Engineer
- SOC Security Analyst
- Network Engineer
- Senior Security Consultant
- Information Security Manager
- Senior SOC Analyst
- Solution Architect
- Cybersecurity Consultant
- Cyber Defense Analyst
- Vulnerability Assessment Analyst
- Warning Analyst
- All-Source Analyst
- Cyber Defense Incident Responder
- Research & Development Specialist
- Senior Cloud Security Analyst
- Third Party Risk Management
- Threat Hunting Analyst
- Penetration Tester
- Cyber Delivery Manager
- Application Security Risk
- Threat Modelling Specialist
- Web Application Penetration Testing
- SAP Vulnerability Management – Solution Delivery Advisor
- Ethical Hacker
- SIEM Threat Responder
- Product Security Engineer / Manager
- Endpoint Security Engineer
- Cybersecurity Instructor
- Red Team Specialist
- Data Protection & Privacy Officer
- SOAR Engineer
- AI Security Engineer
- Sr. IAM Engineer
- PCI Security Advisor
- Exploitation Analyst (EA)
- Zero Trust Solutions Engineer / Analyst
- Cryptographic Engineer
- AI/ML Security Engineer
- Machine Learning Security Specialist
- AI Penetration Tester
- AI/ML Security Consultant
Current CEH Batch
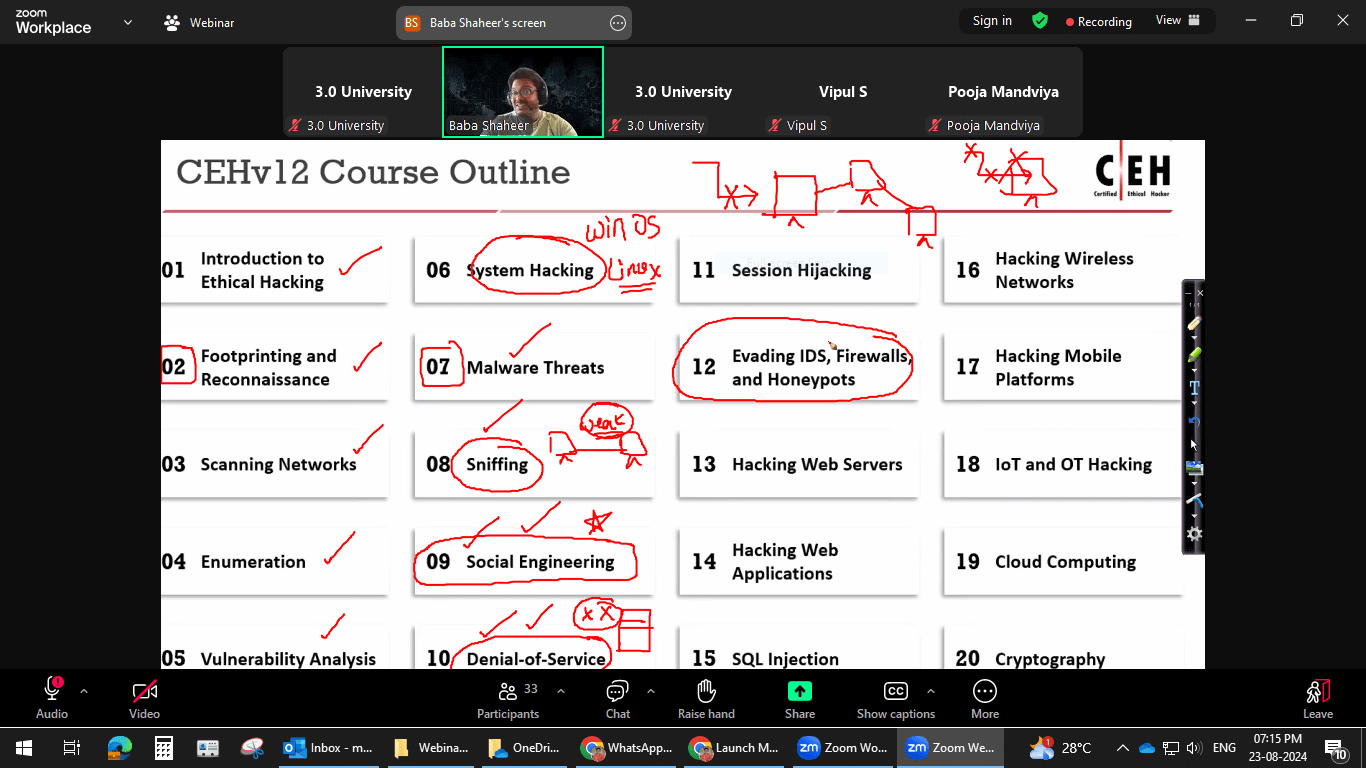
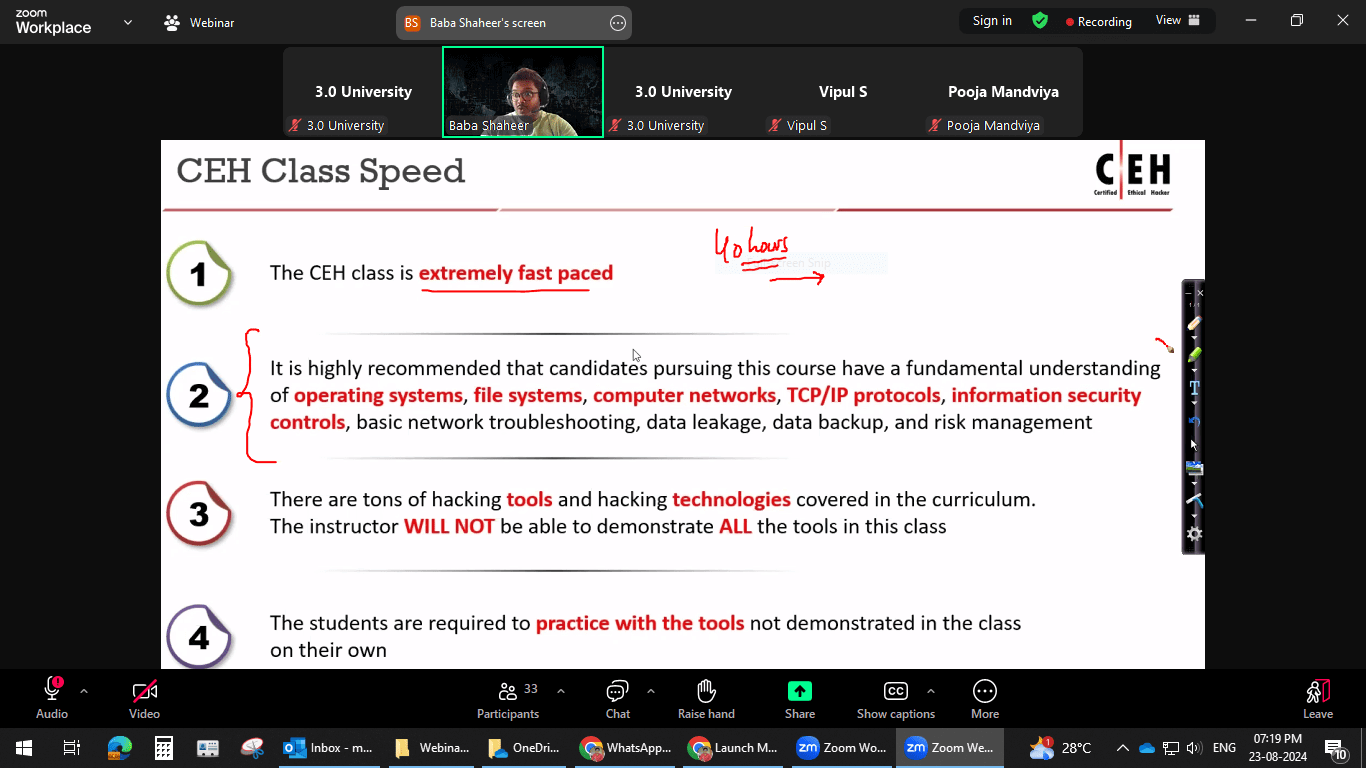
Join the Journey to Become a Certified Ethical Hacker
- Secure Your Spot for CEH v13 Now
Why Join Us?
- Expert-Led Training: Learn from seasoned cybersecurity professionals who bring real-world insights into the classroom.
- World-Class Curriculum: Aligned with the latest industry standards to provide real-world expertise.
- Internship Opportunities: Get a chance to intern with the leading cybersecurity companies. Providing a platform to kickstart your cybersecurity career.





Career Launchpad
Become a CEH Professional with 3.0 university and get an opportunity to intern with the Leading Industry Practitioners
Who is CEH for ?
- Working Professionals: CEH empowers working professionals to enhance their cybersecurity skills and advance in today's competitive tech landscape.
- Students: CEH provides students with a solid foundation in ethical hacking, preparing them for lucrative careers in cybersecurity.
- Cybersecurity professionals: Drive your cybersecurity career forward with CEH, enhanced by the power of Al
- Teams and organizations: Turbocharge your team's knowledge with certified ethical hacking powered by Al
Your Lead Instructor
MR. BABA SHAHEER
Professional Experience
- Cybersecurity Consultant & Senior Consultant
- Researcher & Cybersecurity Instructor
- Mentorship and Professional Development
Certification Completed
Key Competence
- Microsoft Certified: Azure Security Engineer Associate
- Microsoft Certified: Cybersecurity Architect Expert
- EC-Council Certified Ethical Hacker (CEH)
- CompTIA Security+ Certification
- Certified EC-Council Instructor
- Computer Hacking Forensic Investigator (CHFI)
- Penetration Testing & Red Team Operations
- Vulnerability Assessment & Secure App
- Training Development & Delivery
- Team Leadership & Project Management
- Risk Management & Compliance
- Computer Hacking Forensic Investigator
Your Lead Instructor
MR. BABA SHAHEER
Professional Experience
- Cybersecurity Consultant & Senior Consultant
- Researcher & Cybersecurity Instructor
- Mentorship and Professional Development
Certification Completed
- Microsoft Certified: Azure Security Engineer Associate
- Microsoft Certified: Cybersecurity Architect Expert
- EC-Council Certified Ethical Hacker (CEH)
- CompTIA Security+ Certification
- Certified EC-Council Instructor
- Computer Hacking Forensic Investigator (CHFI)
Key Competence
- Penetration Testing & Red Team Operations
- Vulnerability Assessment & Secure App
- Training Development & Delivery
- Team Leadership & Project Management
- Risk Management & Compliance
- Computer Hacking Forensic Investigator
What our learners are saying

Prathamesh yadav
I secured a job as a Cyber Security Analyst, thanks to the CEH course! The course exceeded my expectations, equipping me with strong technical skills that directly helped me in my interview. Special thanks to Sir Baba Shaheer for his excellent teaching. I highly recommend 3.0 university to anyone looking to build a career.

Piyush Varughese
The CEH v12 course, instructed by Baba Shaheer, was an excellent experience. His deep knowledge and engaging teaching style made complex topics easy to understand. The practical labs and real-world examples enhanced my skills and confidence in ethical hacking. Highly recommend for anyone pursuing cybersecurity.

Utkrisht Verma
I extend my appreciation for the valuable academic experience provided. The courses have been profoundly informative, broadening my understanding in ways previously unforeseen. I am thankful for the opportunity to participate in an institution that embraces progressive ideologies and fosters innovation.

Malastar Ayush
Everything is going great in my Certified Ethical Hacker Program! Faculty are quite good; they provide notes every day and hold lectures on time. Beyond the course material, they shares the most recent information and tools, and the support section is always available to assist. Continue your fantastic effort!

Samudra Banerjee
I participated in the Cybersecurity program at 3.0 University, led by Love Babbar Sir. His expertise made complex topics engaging, enhancing my understanding of data structures and algorithms. The university's commitment to emerging technologies provided up-to-date resources. Additionally, program manager Vipul offered invaluable guidance, reflecting his dedication to a positive learning experience.

Prathamesh Yadav
I secured a job as a Cyber Security Analyst, thanks to the CEH course! It exceeded my expectations, providing strong technical skills that helped me ace my interview. A special thanks to Sir Baba Shaheer for his exceptional teaching. I highly recommend 3.0 University to anyone looking to start a career in cybersecurity. This course truly made a difference for me!

Swetanshu Agrawal
Enrolling in the Cybersecurity program at 3.0 University was transformative. Love Baba Sir’s expertise made complex topics engaging, while the curriculum’s real-world focus strengthened my skills. Vipul’s mentorship and 3.0 University’s innovative approach provided invaluable support, making every challenge an opportunity. This experience truly fueled my passion for learning.

Piyush Varughese
The CEH v12 course with Baba Shaheer was an outstanding experience. His deep knowledge and engaging teaching made complex topics easy to grasp. The hands-on labs and real-world examples boosted my skills and confidence in ethical hacking. I highly recommend this course to anyone looking to build a strong foundation in cybersecurity and advance their career.

Sahas Singh
My passion for cybersecurity drove me to specialize in penetration testing, vulnerability assessments, and network security. Under Baba Sir’s training, I gained hands-on expertise in ethical hacking. 3.0 UNi’s structured curriculum and Vipul Sir’s mentorship were invaluable. Scoring 110/125 on my first attempt reflects the strong foundation I built, preparing me for a successful cybersecurity career.

Utkrisht Verma
I sincerely appreciate the valuable academic experience provided. The courses were highly informative, expanding my understanding in ways I hadn’t imagined. I'm grateful for the opportunity to be part of an institution that embraces progressive ideas and fosters innovation. This experience has truly enriched my knowledge and prepared me for future challenges in my field.

Sai Prashanth
The CEH course was a game-changer. Baba Sir simplified complex concepts, making learning enjoyable. Each session was engaging, and 3.0 Uni provided excellent support. Vipul ensured a smooth journey throughout. This course enhanced my skills, confidence, and practical knowledge, making it a truly enriching and career-defining experience. I highly recommend it to anyone pursuing cybersecurity.

Malastar Ayush
My Certified Ethical Hacker program is going great! The faculty is excellent, providing daily notes and timely lectures. Beyond the syllabus, they share the latest tools and industry updates. The support team is always available to help, making learning seamless. Their dedication and expertise have made this journey enriching. Kudos to the team for their fantastic efforts!
C|EHv13 Exam & Certification
CEH v13 introduces several advancements, including:
- AI-powered cyber-attacks, IoT, and cloud security trends.
- Interactive hands-on labs and real-world scenarios.
- Extensive coverage of emerging tools and advanced attack vectors.
- Real-time exposure to modern cybercrime trends and techniques.
While there are no mandatory prerequisites, it is recommended that candidates have a basic understanding of networking, operating systems, and cybersecurity fundamentals.
CEH v13 certification provides several career advantages:
- Globally recognized validation of ethical hacking skills.
- Enhanced employability for roles such as Ethical Hacker, Security Analyst, Penetration Tester, etc.
- In-depth knowledge of advanced techniques in cyber threat defense.
Participants will receive:
- Official EC-Council courseware and eBooks.
- Access to iLabs, offering a platform for practical, hands-on experience.
- Realistic simulations of hacking scenarios.
- Ongoing mentorship and support throughout the course.
Yes, we offer comprehensive career support, including:
- Resume building and interview preparation.
- Job placement assistance ensuring graduates and working professionals are well-prepared for the cybersecurity job market.

Enroll Now
Take the first step towards a rewarding career in cybersecurity. Enroll in the ethical hacking course online in India offered by 3.0 University and accredited by EC-Council. With our industry-leading training and certification, you'll be well on your way to becoming a top-tier ethical hacker.
Don't miss out on this opportunity to join the best Ethical Hacking Course in India.
Enroll now and become a Certified Ethical Hacker with the skills and knowledge to protect and secure digital assets.
Special Scholarship for Students
Few Seats Remaining, Enroll Now
Corporate Discounts for Working Professionals
Accredited Training Center

Accreditations, Recognitions and Endorsements


























































