
AI-Driven Cyber Threats
- Posted by 3.0 University
- Categories Artificial Intelligence
- Date April 16, 2025
- Comments 0 comment
Tech evolution has sparked a sequence of breakthroughs that mix promise with real risks. Artificial intelligence has become a prominent feature in this mix, simplifying everything from routine operations to specialized fields such as cybersecurity.
Yet as companies increasingly lean on these smart systems, they often, perhaps unintentionally, leave their defences open to threats that use the same tech for harmful purposes.
Traditional security measures are struggling to keep up as adversaries use machine learning to rapidly identify and exploit vulnerabilities.
Let’s also delve into the types of recent AI cyber-attacks.
Recent examples of AI-powered cyberattacks clearly demonstrate this shift, enabling hackers to automate their plans, pinpoint specific targets, and even adapt their attacks dynamically.
Take, for example, the flowchart that outlines data analysis and anomaly detection—it nicely illustrates how such processes, when misused, can help bad actors slip standard past security measures and launch custom attacks.
Overall, understanding this double-edged nature of AI is crucial, in most cases, if we’re going to get ready for the next surge in cybersecurity challenges.
The Rise of AI Cyber Attacks
Artificial intelligence is shaking things up in ways we didn’t expect. Artificial intelligence not only fosters creativity but also exposes organizations worldwide to new vulnerabilities.
Cybercriminals are now, quite literally, using AI—mixing in machine learning tricks—to refine their tactics and automate their system breaches.
This improvement isn’t just a minor tweak; it’s a total shift from the old-school methods to these slick, AI-enhanced manoeuvres. Recent AI-powered cyberattacks have shown that hackers target not only data theft but also system weaknesses with a kind of surgical exactness.
Fred Kwong, DeVry University’s chief information security officer, generally remarks that AI is fast becoming the next arena in the cybersecurity battle.
By now, we all have realised that for organisations and businesses to remain competitive, they will have to amass investments enormously in AI, even as the same tech is increasingly used to attack them.
All things considered, it genuinely underscores the extreme need for stronger cybersecurity measures that can spot and neutralize these emerging threats.
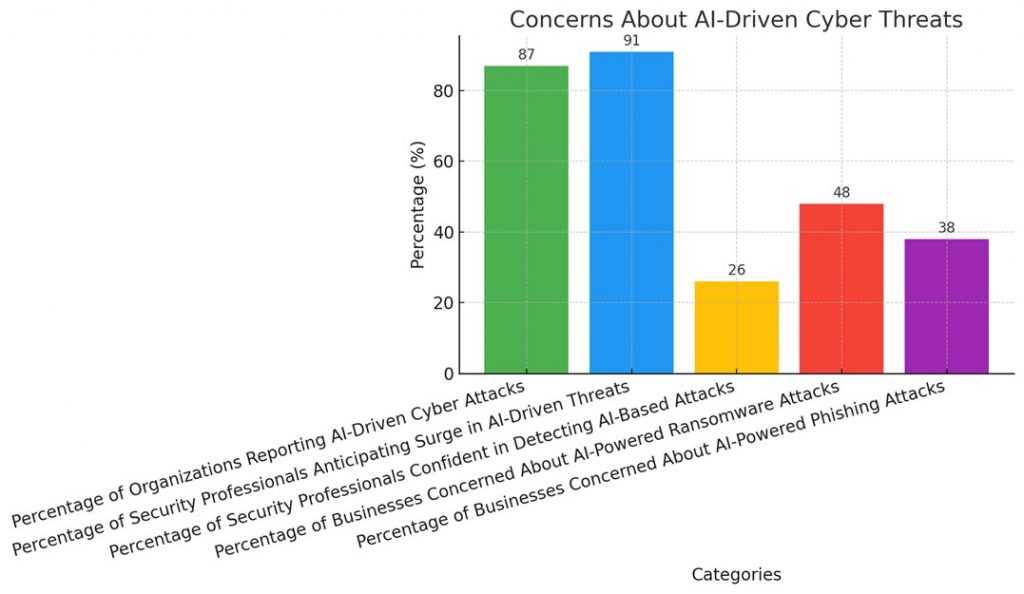
The chart explains concerns pertaining to AI-driven cyber threats, highlighting the significant percentages of organizations reporting AI attacks and security professionals anticipating an increase in AI threats.
It also shows the low confidence levels in detecting such attacks and the growing concerns about AI-powered ransomware and phishing attacks.
The data featuring in the chart above point up the urgent need for improved cybersecurity measures in the face of evolving AI-related challenges.
Recent AI Cyberattacks and Their Implications
AI-powered attacks are now a significant aspect of cybersecurity, underscoring the need for more robust protection.
Recently, we’ve noticed attackers using smart computing and automated tricks to launch assaults with a speed and sharpness that’s almost difficult to believe.
Occasionally, these incursions—ranging from auto-phishing to intricate ransomware attacks—do more than just pry into sensitive info; they can also knock vital services offline, leaving organizations with hefty bills.
There’s this detailed flowchart that lays out how data gets checked and oddities spotted, which kind of underscores why having strong cybersecurity setups is so important.
Tracing the path of detecting these threats reveals that IT professionals are grappling with a complex issue—AI can enhance defences while simultaneously arming attackers.
All in all, a balanced approach that boosts safeguards while keeping an ever-watchful eye out for new dangers is essential if we’re going to handle the next wave of AI-driven cyber threats.
How Hackers Are Using AI for Cyber Attacks?
Technology sneaks into almost every part of our daily lives these days, and with it comes a sweeping change in how we face cyber threats.
AI-backed attacks have emerged, enabling hackers to quickly sift through vast amounts of data to identify system vulnerabilities.
Now, AI tools can hunt out vulnerabilities faster than old methods ever could—cutting down attack time dramatically.
Often, machine learning lets these attackers constantly tweak their moves, shifting tactics on the fly as defenses get stronger.
Experts are left scratching their heads in cases where programs mimic regular user behavior so well that they evade security checks.
Generally speaking, these developments push us to question our old-school defenses and reconsider how we protect our digital world.
This shift is nicely shown in , which lays out the complex process of data analysis and detection that even clever AI can outsmart—emphasizing, if you will, the need for smarter cybersecurity tactics.
Conclusion
Cybersecurity isn’t the same as it once was—companies now have to act before things go south rather than merely reacting afterward.
In most cases, AI-powered attacks have completely changed the landscape; these threats leverage machine learning and automation to increase their speed and effectiveness, surpassing the capabilities of traditional methods.
Recent events have demonstrated hackers integrating AI into multi-layered operations, processing vast amounts of data, and making instantaneous decisions that surpass human reaction times.
Firms, then, really need to get a solid handle on these AI techniques—take, for instance, the anomaly detection frameworks presented in the image.
All of them, invariably, offer a kind of hands-on, if not thoroughly organized, peer closely and meticulously at how to identify and deal with threats as they evolve.
Largely, being dependent on smart strategies and adopting cutting-edge technology will, seemingly, be the most effective method to prepare for the upcoming wave of AI-driven cyber threats, ensuring defences remain ahead of constantly evolving adversaries.
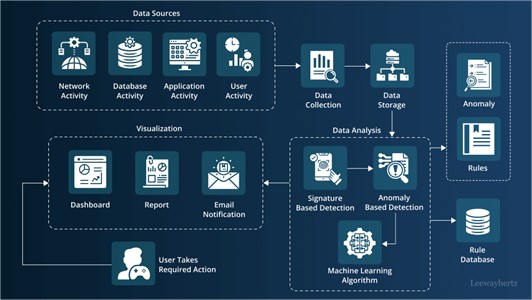
Image1. Flowchart of Data Analysis and Anomaly Detection Process
You may also like

AI Education and Job Market in 2025

What is the Role of AI in the Metaverse?

