
Zero Trust Architecture: The Future of Enterprise Security
- Posted by 3.0 University
- Categories Emerging Technology
- Date April 15, 2025
- Comments 0 comment
What is Zero Trust Architecture?
In the present times, cybersecurity is rapidly changing, and Zero Trust Architecture (ZTA) has emerged as a significant innovation that challenges traditional security concepts.
Instead of leaning on the familiar perimeter defences, ZTA simply insists that nothing should be assumed safe; every user, no matter where they connect from, has to prove their identity first.
That “never trust, always verify” idea isn’t just a catchy slogan—it’s a rule that forces every access attempt to get its proper check.
You can even see how this process plays out in the dynamic flowchart encapsulated in the image, which kind of lays out, step by step, the many verifications involved.
Layers of protection now cover devices, applications, data, and networks, which in most cases helps address the weaknesses that come with remote work and cloud setups.
Plus, by melding continuous monitoring with flexible access controls, security measures tend to keep evolving as new threats emerge, however unpredictable they might be.
In the end, as companies scramble to protect their sensitive information against increasingly clever cyberattacks, grasping and applying the core ideas behind Zero Trust Architecture turns out to be absolutely critical for navigating today’s complex, ever-changing security landscape.
Why Enterprises Need Zero Trust Architecture?
What are the methods of Securing Modern Enterprises is a perpetual question, and this piece, seemingly, looks through the near solutions.
Cyber threats are ramping up—not only in how often they occur but also in their crafty nature—so the old idea of just setting up a secure perimeter isn’t doing the trick for keeping vital company data safe.
Nowadays, as businesses shift and change, it’s clear that no one—user or device—deserves automatic trust, whether they’re working from the office or logging in remotely.
Zero Trust Architecture (ZTA) steps in here with its simple yet firm idea: don’t assume anyone is safe until you double-check.
In most cases, when companies adopt ZTA, they really dial down their risks by enforcing tight controls on who gets in, checking identities repeatedly, and breaking the network into small, closely monitored chunks.
Remote work and booming cloud services only mix up the security game even more, nudging organizations to lean into ZTA as a must-do rather than a nice-to-have.
All in all, shifting to a Zero Trust mindset isn’t just a smart move—it’s essential in fighting off today’s ever-evolving cyber threats.
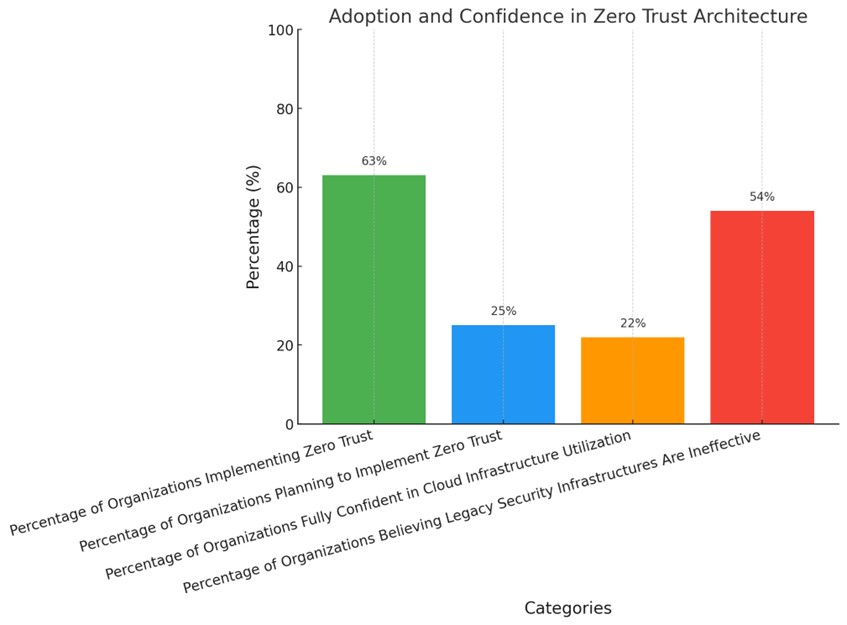
This chart illustrates the adoption levels and confidence among organizations regarding Zero Trust Architecture (ZTA). It shows that 63% of organizations have implemented ZTA, while an additional 25% plan to do so.
Despite this progress, only 22% of organizations express full confidence in utilizing their cloud infrastructure, and 54% believe legacy security infrastructures are inadequate against cyber threats, highlighting the necessity for ZTA to tackle these issues.
Benefits of Zero Trust Architecture
Cybersecurity is changing so fast these days that companies just have to step up their security checks.
Zero Trust Architecture (ZTA) is all about that—it’s built on the idea that you never assume trust but have to keep proving it over and over.
This way of working not only cuts down the risk of unauthorized access but, in most cases, helps organizations stick to the rules they’re supposed to follow.
With cyberattacks growing cleverer and elaborate, ZTA limits access strictly so that people get only the data they actually need; nothing extra is handed over by default.
As stated, “Zero Trust Architecture (ZTA) is a never trust, always verify concept to improve cybersecurity by eliminating trust and validating network requests continuously.”
The visual representation further shows that every single interaction on the network is scrutinized—each access request kicks off its own rigorous authentication process that really bolsters overall security.
In the end, switching to ZTA strengthens defences and fosters a kind of everyday security awareness throughout the whole organization.
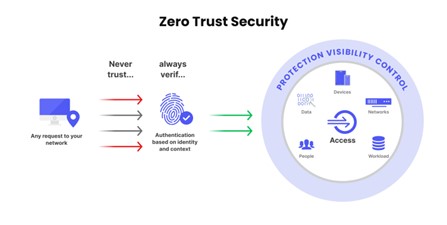
Image1. Visual representation of Zero Trust Security principles and components.
Benefit | Statistic |
Cost Reduction | Implementation of Zero Trust Architecture leads to an average reduction of $684,000 in risk impact over four years for small to medium-sized organizations. |
Enhanced Data Protection | Zero Trust Architecture ensures secure, real-time mission data delivery while denying adversaries access to critical systems, even if networks are compromised. |
Improved Situational Awareness | Zero Trust Architecture provides more visibility into resource usage, improving the detection of attacks and leading to more timely responses. |
Increased Adoption | In just two years, adoption of Zero Trust Architecture has more than doubled, with 61% of organizations now having a defined Zero Trust initiative in place. |
Zero Trust Architecture Benefits and Adoption Statistics
Challenges of Implementing Zero Trust
Transitioning to a Zero Trust Architecture (ZTA) presents a complex array of challenges that companies must navigate to enhance their security measures.
One big hurdle comes from trying to blend these fresh, modern ideas with older, clunkier systems; older infrastructures often just don’t offer the kind of flexibility ZTA needs.
Then there’s the matter of pushback from team members who, in most cases, are so comfortable with traditional security models that any change can really slow things down.
The ongoing demand for constant authentication and monitoring ends up cranking up every day operational pressures, leaving folks to fret about how to best apportion resources and expert know-how.
When you add up all these issues, it’s clear that open communication and solid training become key to nurturing a culture that can actually embrace Zero Trust.
As illustrated, the tangled mix between various security policies and the ways they’re enforced only drives home the point that organizations must get a good grip on these dynamics if they hope to succeed.
Ultimately, addressing these challenges head-on is not just a choice, but a necessity for any organization seeking to safeguard its networks against constantly evolving threats.
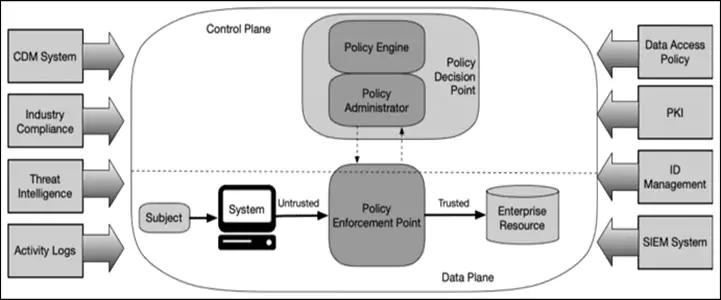
Image2. Cybersecurity Architecture: Control Plane and Data Plane Interaction
Challenge | Description |
Lack of IT Expertise | Many organizations face difficulties due to insufficient knowledge and skills required to implement Zero Trust principles effectively. This gap can lead to misconfigurations and security vulnerabilities. ([nitaac.nih.gov](https://nitaac.nih.gov/resources/articles/zero-trust-paving-road-secure-network-perimeter?utm_source=openai)) |
Integration with Existing Infrastructure | Integrating Zero Trust with legacy systems and technologies can be complex and costly, as existing infrastructures may not be designed to support Zero Trust models. ([gao.gov](https://www.gao.gov/products/gao-23-106065?utm_source=openai)) |
Resource Constraints | Implementing Zero Trust requires significant resources, including computing power, new tools, and training, which can be expensive and time-consuming. ([gao.gov](https://www.gao.gov/products/gao-23-106065?utm_source=openai)) |
Interoperability Issues | Achieving seamless integration between various technologies and vendors is challenging, as there is no single Zero Trust solution, leading to potential compatibility issues. ([gao.gov](https://www.gao.gov/products/gao-23-106065?utm_source=openai)) |
Evolving Standards and Frameworks | The lack of established governance frameworks and technical standards for Zero Trust means organizations must navigate an evolving landscape without clear guidelines. ([gao.gov](https://www.gao.gov/products/gao-23-106065?utm_source=openai)) |
Comprehensive Asset Inventory | Organizations often lack a complete understanding of their network components, information systems, and user behaviors, making it difficult to implement effective Zero Trust measures. ([govinfosecurity.com](https://www.govinfosecurity.com/nist-says-federal-agencies-struggling-to-achieve-zero-trust-a-23736?utm_source=openai)) |
Challenges of Implementing Zero Trust Architecture
Conclusion
Zero Trust architecture is transforming the traditional enterprise security approach.
Instead of thinking your internal network is automatically safe, threats now crop up both inside and out—so you end up having to verify everything all the time. Let’s also discover what are the future trends in Zero Trust.
This change shows itself in a constant need to check identities and keep an eye on devices, kind of like that detailed flow of policy enforcement in the image.
It brings together things like data, networks, and even applications into one big protective mix.
In many cases, while you get better breach protection and smoother compliance with data rules, you also face extra complexity and sometimes even pushback against change.
All in all, as organizations stumble their way through these shifting times, leaning into Zero Trust isn’t just a good idea—it’s pretty much essential if you want to stand up to increasingly clever cyber threats.
And including references such as those shown in the accompanying image really shows how key it is to verify identities, pushing us all to keep rethinking our security setups.
Some of the Key Components of Zero Trust Architecture are stated below, in the image.
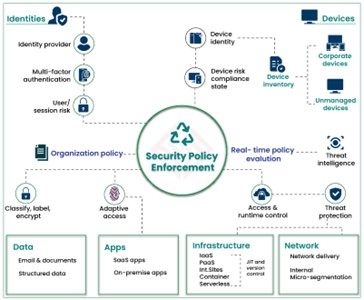
Image3. Flowchart of Security Policy Enforcement Components
You may also like

How 3.0 University Prepares You for Future Jobs?

How to Build a Career in IoT?

